Hail Caesar
February 4, 2021
A very old encryption method is the Caesar Cipher.
For testing purposes, usually the ASCII code is used.
But you can add a little more security to your message.
For example:
Rules: Shift all letters by 5
Plain Text: Attack at midnight.
Apply the rules.
Cipher text: Fyyfhp fy rnisnlmy.
One solution: Give the letters a random number, or use some fake numbers in between to confuse the spy.
The main problem is that same letters are the same after encryption.
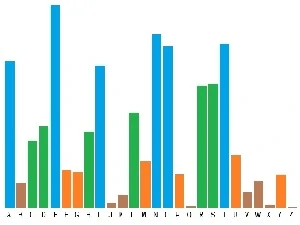
An attacker (f/m/d) could find some letters due to their "letter frequency".
The letter frequency varies in different languages, books, special texts or in dictionaries.
Some recent child names increase the rare letters.
A letter frequency diagram:
Now you could use a letter for the "space" between the words, or shift the second word by increasing with one.
Rules: space = R, "shift-start" with 5 and increase by 1 each word.
Plain Text: Attack at midnight.
Now with the new rules.
Cipher text: FyyfhpRgzRtpkupnoa.
Next step: Transfer the "key" to your colleague.
In case your name is Bob, your mate is called Alice.
Those are the most used names in illustrations. A and B...
The main problems with a symmetric algorithm is that you decode and encode with the same key and you need to send the key together with the message.
Or a second way: The security level of your "key" depends on the safe transmission of your key to a friend.
An evil dude should not take a look, in case you send the key with a "secure" postcard or letter.
A real help gives us an asymmetric cryptography algorithm. But that's an other story.